All about Networking

Basic Networking Tutorial -  Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
 Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
Basic Networking Tutorial - a network is any collection of independent computers that communicate with one another over a shared network medium.A computer network is a collection of two or more connected computers. When these computers are joined in a network, people can share files and peripherals such as modems, printers, tape backup drives, or CD-ROM drives.
Remote Desktop Technology of Windows XP -  Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
 Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
Some people thought that the whole notion of terminal services is a bit to technical for them to understand. Well, MicroSoft and our good friends that work for Bill Boy Gates have come out with terminal services, changed the name and made it a whole lot easier to understand. Find out how!
How IPV-6 Is Going To Change the Net -  Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.
Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.
 Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.
Ever wonder what'll happen when all the possible IP addresses will be taken? Remember when the phone companies ran out of 800 numbers? Well the same thing is about to happen with IP addresses and quickly. With IP V-6 every person on earth could have a million uniquely addressees and the individually locatable IP devices Read all about it here.
Most Common TCP Ports -  TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
 TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
TCP ports will popup almost with any application you use wether it is ICQ or FTP. It will soon be realized how good its knowledge is once you yourself will start applying it in day to day tech use. TCP/IP uses several protocols, the two main ones being TCP and IP.
How Virtual LANs (VLANS) Work - 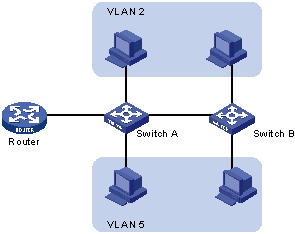 A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
 A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
A VLAN is a grouping of computers that is logically segmented by functions, project teams, or applications without regard to the physical location of users. Similar to routers, VLANs offer an effective mechanism for setting up firewalls in a switch fabric, protecting the network against broadcast problems that are potentially dangerous, and maintaining all the performance benefits of switching. You can create these firewalls by assigning switch ports or users to specific VLAN groups in single switches and across multiple connected switches, which will increase security easily and inexpensively by segmenting the network.
Improving Performance Over Wireless Networks -  TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen.
TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen.
 TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen.
TCP is a common transport protocol that is used in almost all the internet applications. The main problem with the TCP is that TCP falsely assume the packet loss as congestion. The TCP sender detects a packet loss when a time out happens or duplicate acknowledgements happen.
Windows Windows on the Wall -  Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network).
Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network).
 Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network).
Windows NT is generally regarded among IT (information technology) professionals as the most stable and secure Windows OS (operating system). Win2000 and WinXP Pro work well in a peer-to-peer network, but these OSes are designed to handle client/server networking, where in multiple clients (computers, or workstations) connect to one or more servers (computers that control the network's software and each client's access to other parts of the network).
Did You Go To My PC? -  Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
 Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
Ever make it just in time for work after driving through rush hour traffic and realize that you've left an important file on your computer at home? Or have you ever had to work late in the office because you don't have access to files, applications, or shared resources at home? Well maybe your life has just become way easier. Introducing, GoToMyPC! A wonderful little service that'll let you access your home or work computer from anywhere! It takes two minutes to download this amazing software onto your computer and you'll have the power to access your computer from any web browser on any computer. A simple little technology of PC-to-PC connection or as GoToMyPC calls it, "Remote-Access Solution" will go a long way for anyone.
Internet Connection Sharing - Part I - 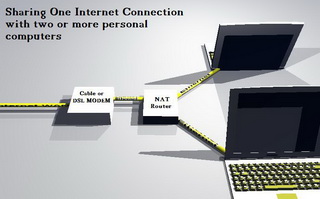 This article explains Internet Connection Sharing in detail, and is designed as a practical guide to help you set it all up. There are many different ways to set up Internet Connection Sharing, but for the purposes of this article, it is assumed that you have two or more computers connected via a hub or switch.
This article explains Internet Connection Sharing in detail, and is designed as a practical guide to help you set it all up. There are many different ways to set up Internet Connection Sharing, but for the purposes of this article, it is assumed that you have two or more computers connected via a hub or switch.

Using the Computer...Away From the Computer -  You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
 You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
You get to work on a Monday morning, and realise that you've left the document you were presenting today back at home on your computer. How do you get it? Or maybe you have a friend that has problems with their computer, and you know how to fix it, but only if you can see it. There could be many more situations where you need to use a particular computer and you're not there. Enter the range of programs known as VNC.
DNS Resolver Cache - 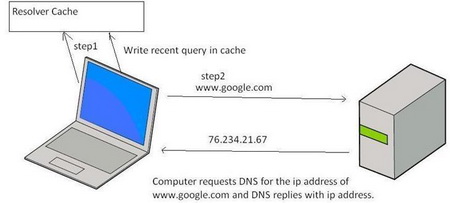 To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
 To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
To help speed up Web browsing, Windows XP comes with a local cache containing any DNS addresses that have been looked up recently. Once an URL has been resolved by an Internet name server into a numerical IP, the information is stored locally. Anytime your browser requests an URL, Windows XP first looks in the local cache to see if it is there before querying the external name server used by your ISP. If it finds the resolved URL locally it uses that IP. This is supposed to save time and cut down on Web traffic.
Wireless Network Security -  Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
 Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Ever wonder if it's a good idea to switch your home LAN to wireless? This is a very easy to understand discussion about the security matters involved.
Internet Backbone Speeds -  This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
 This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
This is something that can come in handy for those of you who are simply curious about internet backbone speeds.
Denial Of Service -  DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
 DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
DoS stand for denial-of-service attack, a type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. While DoS attacks do not usually result in information theft or any security loss for a company, they can cost an organization both time and money while their network services are down.
Kindness Online -  So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
Now, it may seem like there is less hope today than there was before. People are less kind. There is less trust around. I don't know. As a simple example, we could run a test here. How many people have ever hitchhiked? I know. How many people have hitchhiked within the past 10 years? Right. So what has changed? It's not better public transportation. So that's one reason to think that we might be declensionists, going in the wrong direction.
 So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.
So I thought this morning I would try to be the optimist, and give reason to hope for the future of the Internet by drawing upon its present.Now, it may seem like there is less hope today than there was before. People are less kind. There is less trust around. I don't know. As a simple example, we could run a test here. How many people have ever hitchhiked? I know. How many people have hitchhiked within the past 10 years? Right. So what has changed? It's not better public transportation. So that's one reason to think that we might be declensionists, going in the wrong direction.

Networking Terms and Topics, Simplified! -  This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
 This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
This very much to the point guide highlights some important networking terms and topics and simplifies them to us, the mere mortals.
How to Connect Two Laptops Using Bluetooth -  Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
 Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
Do you need to copy a heavy file from another laptop without using pen drive or connecting cables? Of course, this can be done by using electronic transfer methods like ftp or online data storage systems. However, these methods are not only time consuming, they often lead to increased data transfer costs. Moreover, what if there is no internet connectivity available in the immediate vicinity? Under such circumstances, you can connect two laptops through Bluetooth and exchange files seamlessly.
227 Categorized CompTIA A Plus Q and A -  CompTIA A+ Certification is widely recognized as the first certificationyou should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.
CompTIA A+ Certification is widely recognized as the first certificationyou should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.
 CompTIA A+ Certification is widely recognized as the first certificationyou should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.
CompTIA A+ Certification is widely recognized as the first certificationyou should receive in an information technology (IT) career. Whether you are planning to specialize in PC hardware, Windows operating system management, or network management, the CompTIA A+ Certification exams measure the baseline skills you need to master in order to begin your journey toward greater responsibilities and achievements in information technology.CompTIA A+ Certification is designed to be a "vendor-neutral" exam that measures your knowledge of industry-standard technology.
Network Topologies - .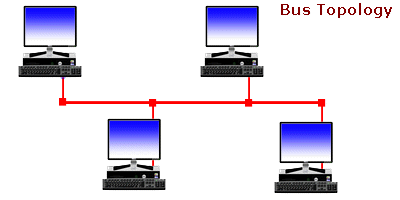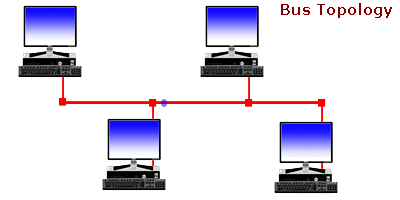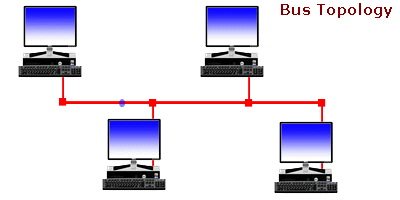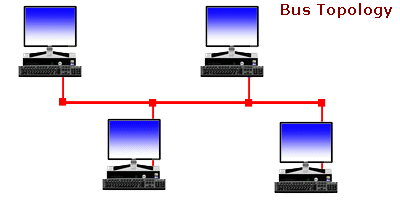 Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them?Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them?Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
 Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them?Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
Ever wonder... how are all of these file, print, fax, and computer resources connected so as to allow the typical desktop computer to access them?Network topology refers to the way networked computers and network resources are connected. The three most widely used topologies are bus, ring, and star. Note that the following network topology diagrams are logical views of the topologies they represent and don’t necessarily match the physical (electrical) interconnections on the networks.
History of TCP/IP -  Internetworking with TCP/IP has been around for many years-almost as many years asUnix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
Internetworking with TCP/IP has been around for many years-almost as many years asUnix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
 Internetworking with TCP/IP has been around for many years-almost as many years asUnix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
Internetworking with TCP/IP has been around for many years-almost as many years asUnix has been available. TCP/IP, or Transmission Control Protocol/Internet Protocol, grew out of the work that was done with the Defense Advanced Research Projects Agency, or DARPA. In 1969, DARPA sponsored a project that became known as the ARPANET. This network mainly provided high-bandwidth connectivity between the major computing sites in government, educational, and research laboratories.
IP Spoofing and Sniffing -  Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
 Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
Sniffing and spoofing are security threats that target the lower layers of the networking infrastructure supporting applications that use the Internet. Users do not interact directly with these lower layers and are typically completely unaware that they exist. Without a deliberate consideration of these threats, it is impossible to build effective security into the higher levels. Sniffing is a passive security attack in which a machine separate from the intended destination reads data on a network. The term "sniffing" comes from the notion of "sniffing the ether" in an Ethernet network and is a bad pun on the two meanings of the word "ether." Passive security attack are those that do not alter the normal flow of data on a communication link or inject data into the link.
WikiLeaks, The Technical Aspect -  Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
 Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Wikileaks has been in the news for quite some time now as it has rocked many nations, embroiling itself in controversy over the fact that it has been releasing classified documents which have been termed as potentially harmful for national security as well as international diplomacy. Amidst all the confusion related to it's ethical and moral standards, people around the world have also speculated how the site functions technically, as a site which has been so controversial, might be technologically sound as well because various steps have already been taken in order to shut the Website down but none of them have availed any results.
Brief History of Wi-Fi -  Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
 Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
Wi-Fi would certainly not exist without a decision taken in 1985 by the Federal Communications Commission (FCC), America's telecoms regulator, to open several bands of wireless spectrum, allowing them to be used without the need for a government license. This was an unheard-of move at the time; other than the ham radio channels, there was very little unlicensed spectrum. But the FCC, prompted by a visionary engineer on its staff, Michael Marcus, took three chunks of spectrum from the industrial, scientific and medical bands and opened them up to communications entrepreneurs.
Implement Chat Systems on an Intranet -  It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
 It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
It used to be that businesses had a major influence on what types of products and services were available to the general public. In the early days of the Internet, networking LAN technologies and needs were the driving force behind the creation of many software applications and tools that users accessed. The growing popularity of the World Wide Web with casual computer users led to a paradigm shift in how to approach usable software solutions for these users. Simple to install and use software applications such as file sharing, e-mail and instant chat programs were instantly popular.
Computer Training Excuses -  You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
 You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
You wouldn't go to a doctor who had never been to medical school, or hire a lawyer who never studied law. One side-effect of a world advancing as rapidly as ours is that fields are becoming more and more specialized and narrow. People can no longer get by on general knowledge in their careers, something I found out for myself not too long ago. I'd been out of high school for two years, scraping by on my own and picking up scraps of programming as I went. I saw all of the self-taught programmers breaking into the IT industry, and I hoped to do the same. After all, IT is one of the few industries out there where being creative and a quick learner is more important than a degree.
Disabling / Enabling Network Adapter -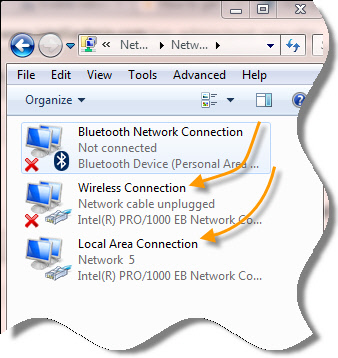 Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.
Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.
I've had this problem for almost a year now but I finally want it stop. All the resources online tell me that it's probably my network driver that may need an update. Well, all my drivers are updated, and the problem still remains. Now What? Okay, I'll be honest... I don't know why it happens but 1 out of every 10 or 12 PC's will come across this problem.
 Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.
Did you recently find out that after your PC starts up fresh, your internet doesn't work? So you probably tried everything and the only thing that seems to work is to disable the "Local Area Connection" (adapter), and then to enable it back again. At least that's what happened to me.I've had this problem for almost a year now but I finally want it stop. All the resources online tell me that it's probably my network driver that may need an update. Well, all my drivers are updated, and the problem still remains. Now What? Okay, I'll be honest... I don't know why it happens but 1 out of every 10 or 12 PC's will come across this problem.

Leaping Ahead in WiFi Standard - 802.11ac -  We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
 We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
We all know that we need more bandwidth now, than we ever did in the past. There tons more online games, online movies, online collab work, you name it. And the past standards of Wifi namely 802.11a, 802.11b, 802.11g, 802.11n, and so on) were getting better and better; however, the 802.11ac does the trick. Well, atleast for now it is, until something better comes along.
How to Assign Static IP Address in Windows Server 2008 R2 - 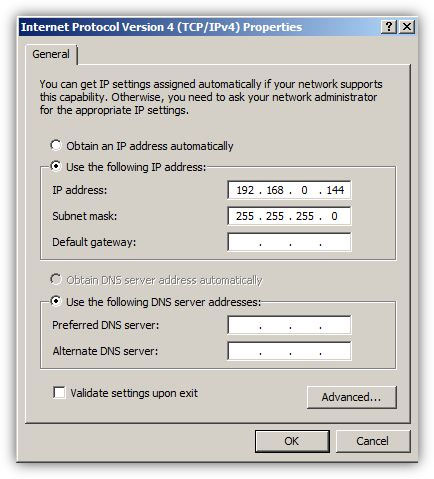 An IP address is a 32-bit number divided in 4 octal numbers and each octal separated by a '.' (dot), technically knows as a period. Administrators assign IP addresses to the computers so that they can be uniquely identified in a local area network and can communicate and exchange information with other computers in the network. IP addresses can be assigned to the computers either manually (static IP addresses) or through DHCP servers (dynamic IP addresses). When administrators plan to assign dynamic IP addresses to the computers they must configure DHCP servers with appropriate IP addressing schemes do accomplish the task. On the other hand, if administrators plan to assign static IP addresses to the computers they must manually go to each computer system in ...
An IP address is a 32-bit number divided in 4 octal numbers and each octal separated by a '.' (dot), technically knows as a period. Administrators assign IP addresses to the computers so that they can be uniquely identified in a local area network and can communicate and exchange information with other computers in the network. IP addresses can be assigned to the computers either manually (static IP addresses) or through DHCP servers (dynamic IP addresses). When administrators plan to assign dynamic IP addresses to the computers they must configure DHCP servers with appropriate IP addressing schemes do accomplish the task. On the other hand, if administrators plan to assign static IP addresses to the computers they must manually go to each computer system in ...

How to Change Windows Server 2008 R2 Computer Name - 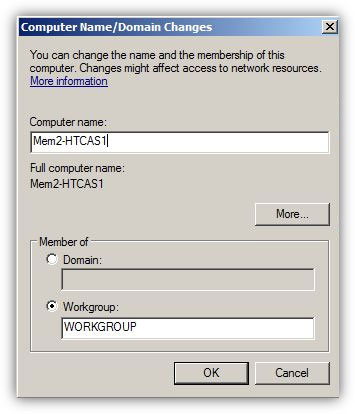 In any computer that runs any operating system of any platform, computer name plays an important role when it comes to its identification. Name that an administrator assigns to a computer must be unique for that computer in the entire network. In case, because of errors or deliberately, administrators assign identical names to 2 or more computers, all the computers with common names stop communicating with other computers in the network. In Microsoft Windows platform computer names are also known as hostnames. When administrators install Microsoft Windows operating systems on the computers, operating systems automatically generate random ...
In any computer that runs any operating system of any platform, computer name plays an important role when it comes to its identification. Name that an administrator assigns to a computer must be unique for that computer in the entire network. In case, because of errors or deliberately, administrators assign identical names to 2 or more computers, all the computers with common names stop communicating with other computers in the network. In Microsoft Windows platform computer names are also known as hostnames. When administrators install Microsoft Windows operating systems on the computers, operating systems automatically generate random ...

How to Promote Windows Server 2008 R2 to a Domain Controller - 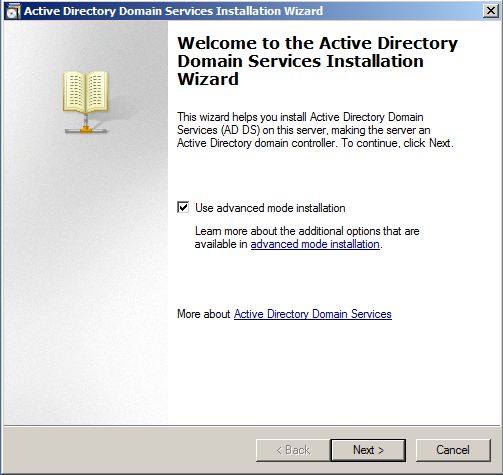 In Microsoft Windows platform all post-Windows 2000 Server network operating systems are shipped along with built-in Active Directory Services (ADS in Windows Server 2003) or Active Directory Domain Services (AD DS in Windows Server 2008) which differentiates them from client operating systems. Although the services are integrated in the network operating systems, they are not automatically installed during the installation of the OS. Because of this when a network operating system is installed on a computer it works as a client operating system and is technically called a ...
In Microsoft Windows platform all post-Windows 2000 Server network operating systems are shipped along with built-in Active Directory Services (ADS in Windows Server 2003) or Active Directory Domain Services (AD DS in Windows Server 2008) which differentiates them from client operating systems. Although the services are integrated in the network operating systems, they are not automatically installed during the installation of the OS. Because of this when a network operating system is installed on a computer it works as a client operating system and is technically called a ...

How to Enable Remote Desktop in Windows Server 2008 R2 - 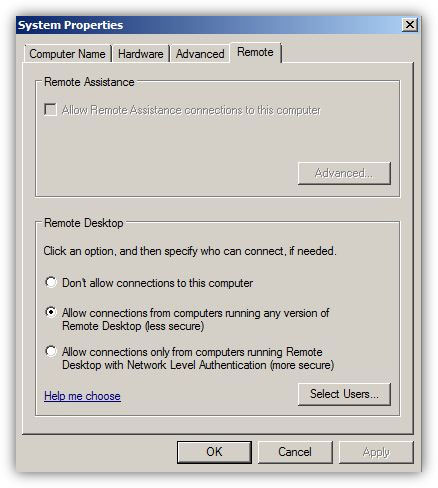 The concept of Remote Desktop was first introduced with the release of Microsoft Windows 2000 (Professional and Server editions) which was then carried forward to all the successor versions of Microsoft-based operating systems. With the help of Remote Desktop administrators can manage remote computers by bringing their entire consoles on the local computer from where they have initiated the Remote Desktop sessions. By using Remote Desktop administrators can administer remote computers as easily and comfortably as they were physically present in front of the remote computers and were locally logged on to them. Since Remote Desktop allows administrators to manage multiple remote machines from single central location, it saves a decent amount of time that administrators would otherwise had to spend if there was no Remote Desktop feature available in the operating systems.
The concept of Remote Desktop was first introduced with the release of Microsoft Windows 2000 (Professional and Server editions) which was then carried forward to all the successor versions of Microsoft-based operating systems. With the help of Remote Desktop administrators can manage remote computers by bringing their entire consoles on the local computer from where they have initiated the Remote Desktop sessions. By using Remote Desktop administrators can administer remote computers as easily and comfortably as they were physically present in front of the remote computers and were locally logged on to them. Since Remote Desktop allows administrators to manage multiple remote machines from single central location, it saves a decent amount of time that administrators would otherwise had to spend if there was no Remote Desktop feature available in the operating systems.

Assigning Multiple DNS IP Addresses on Windows Server 2008 R2 - 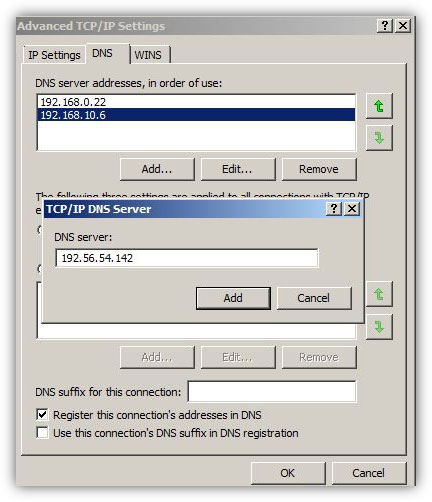 In medium or large-scale organizations where there are several client computers connected to a network, administrators install multiple DNS servers in order to load balance the traffic and to reduce the burden on a single DNS server. Moreover, if there are multiple DNS servers configured in such network scenarios it is likely that administrators might have configured one DNS server as DNS forwarder and have configured other DNS servers to forward the queries to the forwarder. This is an efficient approach that almost all administrators take for error free and smooth name resolution process.
In medium or large-scale organizations where there are several client computers connected to a network, administrators install multiple DNS servers in order to load balance the traffic and to reduce the burden on a single DNS server. Moreover, if there are multiple DNS servers configured in such network scenarios it is likely that administrators might have configured one DNS server as DNS forwarder and have configured other DNS servers to forward the queries to the forwarder. This is an efficient approach that almost all administrators take for error free and smooth name resolution process.

Installing DHCP Server Role on Windows Server 2008 R2 - 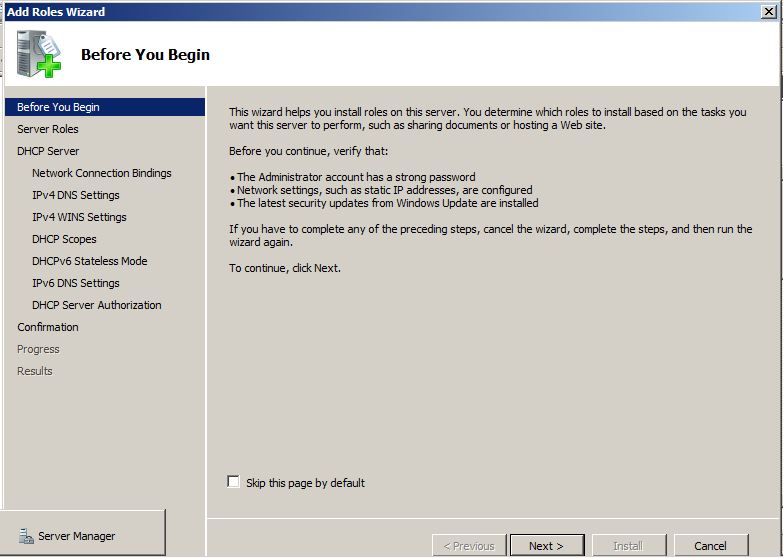 When Windows Server 2008 R2 computer is configured as a DHCP server, it can have multiple NICs and each NIC can be configured to provide IP addresses to the computers that belong to different subnets. For example, if Windows Server 2008 R2 DHCP server has NIC-1 with 192.168.0.22 and NIC -2 with 192.168.1.22 static IP addresses assigned to them, both NICs, if configured appropriately, can provide dynamic IP addresses to the clients connected to their respective subnets.
When Windows Server 2008 R2 computer is configured as a DHCP server, it can have multiple NICs and each NIC can be configured to provide IP addresses to the computers that belong to different subnets. For example, if Windows Server 2008 R2 DHCP server has NIC-1 with 192.168.0.22 and NIC -2 with 192.168.1.22 static IP addresses assigned to them, both NICs, if configured appropriately, can provide dynamic IP addresses to the clients connected to their respective subnets.

How to Share a Folder in Windows Server 2008 R2 - 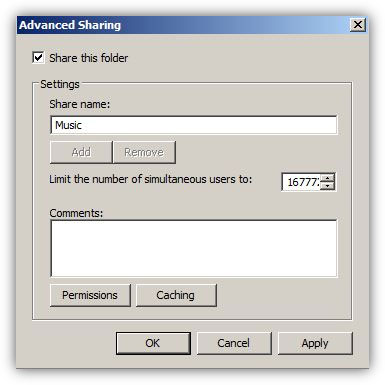 In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
 In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
In organizations or home setups where there are multiple computers connected to each other, in order to transfer files from one computer to another administrators use to share the folders on one computer (generally known as file server) and make them accessible from all other computers in the network. In order to do so administrators normally configure and set NTFS and share permissions on the shared folders which, as a result, help them control the accessibility of user accounts or groups on them.
How to Share Printer in Windows Server 2008 R2 - 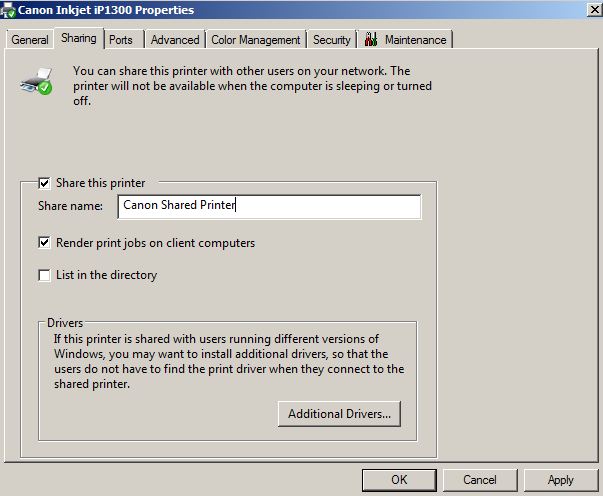 Just like folder sharing in Microsoft Windows operating systems, printer sharing is also an important part in any complex network setup or in simple networking in homes. In either case mostly one printing device is bought and is shared among all the computers connected to the network. Since printing devices, sometimes, are expensive sharing them among all computers in networks is a cost effective approach for both administrators and home users.
Just like folder sharing in Microsoft Windows operating systems, printer sharing is also an important part in any complex network setup or in simple networking in homes. In either case mostly one printing device is bought and is shared among all the computers connected to the network. Since printing devices, sometimes, are expensive sharing them among all computers in networks is a cost effective approach for both administrators and home users.

Add New Host (A) Record in W2K8R2 DNS Server - %20Record.JPG) In any network setup DNS server plays an important role as it helps client computers to resolve names to their respective IP addresses. When a DNS server is installed in a network it automatically creates a Forward Lookup Zone and adds some records in it by its own. A DNS server can have several record types depending on the type of network.
In any network setup DNS server plays an important role as it helps client computers to resolve names to their respective IP addresses. When a DNS server is installed in a network it automatically creates a Forward Lookup Zone and adds some records in it by its own. A DNS server can have several record types depending on the type of network.

How to Map Network Drive in Windows Server 2008 R2 - 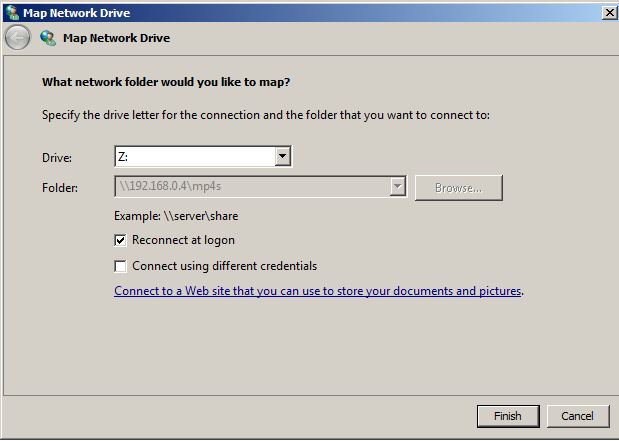 Network drive mapping is a process in which users create shortcuts of shared folders on their local computers. Shared folders can be located anywhere in the network. Shortcuts that users create appear in Computer (in Windows Vista and above operating systems) and My Computer (in pre-Windows Vista operating systems) window.
Network drive mapping is a process in which users create shortcuts of shared folders on their local computers. Shared folders can be located anywhere in the network. Shortcuts that users create appear in Computer (in Windows Vista and above operating systems) and My Computer (in pre-Windows Vista operating systems) window.

Analysis of Network Computer Monitoring Software -  The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...
The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...
 The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...
The most popular application of computer monitoring software is on office networks in a business establishment, where each workstation is actively monitored to see how the employees spend their entire work day.Business applications of computer monitoring software essentially draw its basic function from the principle that increasing the potential productivity could generate a more positive flow in business. In a sense, the computer monitoring software here is regarded as a "performance balancer", by keeping an eye on employees and making sure that they ...
Specify Users' Logon Time in Windows - 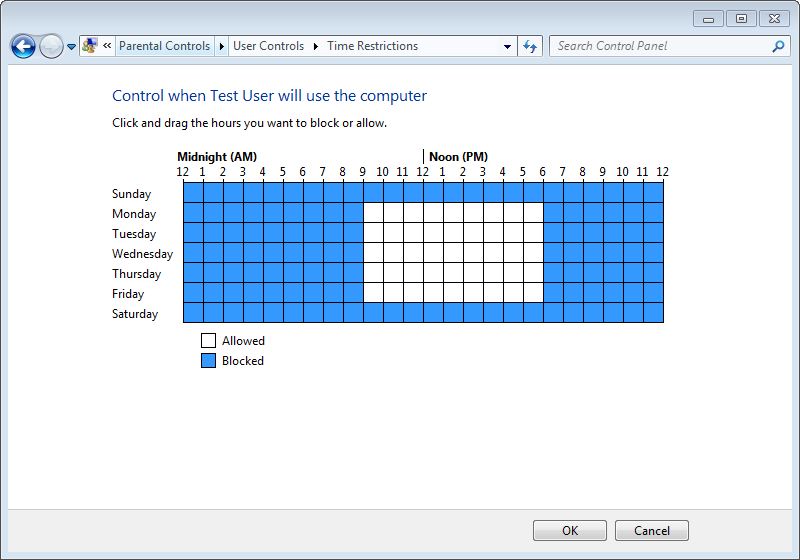 Logon time is the duration between which the operating system allows user accounts to logon to the computer. Logon time can be configured on the operating system only by the administrators of the computer. User accounts that belong to non-admin groups cannot modify or define the logon time and are only allowed to logon to the computer at the times specified for them by the administrators.
Logon time is the duration between which the operating system allows user accounts to logon to the computer. Logon time can be configured on the operating system only by the administrators of the computer. User accounts that belong to non-admin groups cannot modify or define the logon time and are only allowed to logon to the computer at the times specified for them by the administrators.

Networking LAN Cables in Detail - 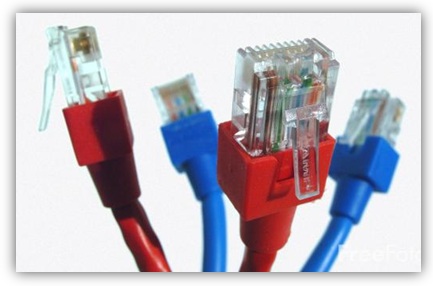 In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
 In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
In any wired LAN environment it becomes necessary to take utmost care while selecting cables for the network setup. Engineers and administrators may select cable types according to the requirements of the LAN setup, budget involved in the infrastructure installation and the scalability of the network. Since cables play important role in any wired network infrastructure it becomes important for the administrators and engineers to select appropriate cable types so as to meet and fulfill the requirements of the organizations.
Understanding Virtualization Concepts -  Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
 Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Virtualization is a process in which a physical computer a.k.a. host computer contains virtual machines that are stored in them in form of files. These virtual machines act exactly the way the physical computers do and can be mapped with the NICs of the host computers. Once mapped, the operating systems installed inside the virtual machines (Guest Operating Systems) can then communicate with the host computers as well as the network setups to which the host computers might be connected.
Understanding Routers -  Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
 Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Routers are the devices that are used to connect two different networks in order to allow communication between them. Networks with different network IDs are considered to be different. By default, no communication can take place between two different networks, and this configuration prevents computers of one network from getting accessed by the computers on the other network, which may belong to another organization, building premises, home, etc.
Understanding LAN Switches -  LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
 LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
LAN switches, which are also sometimes called intelligent hubs, are the networking devices that have completely dominated and replaced Hubs. The reason behind this is that unlike Hubs, that only used to regenerate the received packets and forward them to all the ports that they had, LAN switches create one-to-one virtual circuits directly to the ports to which the destination computers are connected. This reduces the time consumed while transferring the data packets from the source computers to the destination ones.
Understanding Firewalls -  A firewall can be thought of as a gatekeeper who has been handed over a list of people whom he must allow to enter into the premises and/or the list of those people whose request to enter the premises must be denied straightforward. Just like the role of a gatekeeper, a firewall monitors incoming and outgoing network traffic to and from a computer system and allows or denies the communication of the computer with other computers that are connected to it via Local Area Network (LAN). Since in network communication, the packets are transported over the cable or through wireless media, a firewall allows or denies the communication on the basis of source ...
A firewall can be thought of as a gatekeeper who has been handed over a list of people whom he must allow to enter into the premises and/or the list of those people whose request to enter the premises must be denied straightforward. Just like the role of a gatekeeper, a firewall monitors incoming and outgoing network traffic to and from a computer system and allows or denies the communication of the computer with other computers that are connected to it via Local Area Network (LAN). Since in network communication, the packets are transported over the cable or through wireless media, a firewall allows or denies the communication on the basis of source ...

Understading Networking Hubs -  Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
 Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Network hubs were the central devices that network administrators used to use to establish a network setup using Star Topologies. Network hubs had multiple RJ-45 ports integrated in them and were used to connect one end of the LAN cables that had RJ-45 connectors crimped to them. The other end of the cables were connected to the RJ-45 ports available on the PCs. Network hubs were available with 4, 8, 16 and 24 ports. Administrators also used to cascade two hubs for larger network setups. Cascading means that one RJ-45 port of one hub connected to ...
Understanding Bus Topology -  n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
 n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
n a nutshell, network topologies are the physical alignments of computers and the way they are connected to each other. For example, if all the computers are connected to each other via a central device (Hub or Switch), the type of topology is Star. Likewise, if all the computers are connected to each other via a main cable, this means it is Bus Topology.
Understanding Star Topology -  Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
 Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Since over a decade, star topologies have been preferred over bus topologies by the administrators. In star topology, a central device (Hub or Switch) is used to connect multiple PCs in a local area network. Central devices that are used in star topologies have multiple LAN ports integrated in them and the PCs are connected to the central devices via patch cables. In most cases patch cables are twisted pair cables that have four twisted pairs (eight wires in all) which are crimped to the RJ-45 connectors. The reason why star topology is mostly preferred nowadays is that it does not provide a single point of failure and is highly scalable. This means ...
Understanding Mesh Topology -  Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
 Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Apart from star topology that is widely used in almost every network environment, the other type of topology that is complex while setting up but provides 100% fault tolerance to the network is Mesh Topology. In this topology, every computer that has to be connected to the network is connected to every computer that is available in the network. For example if there are four computers namely A, B, C and D, then A will be connected to B, C and D. Likewise B will be connected to A, C and D and so on. This means that when mesh topology is used while establishing a network setup, it is very unlikely that the network would ever face congestions or would ever fail.
Understanding Ring Topology -  In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
 In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
In ring topology, data used to transfer in the form of ring where every computer that was connected to the network had two LAN cards and each LAN card was connected to the LAN card of its neighbor computer. Many times ring topology was preferred over bus topology because there were no collisions and the chances of network getting congested were next to 0%.
Understanding Collision and Broadcast Domains -  In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
 In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
In computer networks, scope (area) up to where data that is transferred over the cables or the wireless media with certain conditions is categorized in two domain main types. In complex network setups, because multiple segments are connected to each other via different types of central devices, it becomes important for the administrators to separate broadcast domains and reduce the numbers of collision domains. A central device in which collisions may occur is Hub because of it logical Bus Topology.
Understanding Wireless Network Topologies -  In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
 In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
In any network setup, network topology plays an important role without which network cannot be established whatsoever. In other words, whenever two or more machines are connected to each other, a topology is automatically formed. Unlike wired networks that have multiple topologies, wireless networks have only two topologies namely Infrastructure and Ad Hoc. Since wireless networks work on unguided media, it makes sense to have limited number of topologies while configuring the wireless network setups. Moreover, since wireless networks are a bit complicated configure as compared to the wired networks, it is essential for the administrators to have ...
Understanding LAN Bridges -  LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
 LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
LAN Bridges were used to separate and isolate multiple collision domains from each other in large broadcast domains. Bridges had two or more LAN ports to which other central devices, such as network Hubs, were connected via LAN cables. Unlike network Hubs that used to forward data packets to every PC that was connected to the ports, Bridges acted more like LAN Switches to identify destination ports and transferred the data packets only if the packets were destined to reach the segments that were connected to their other ends. Bridges used to calculate and identify the destination segments on the basis of physical (MAC) addresses of the central devices that were connected to their LAN ports.
Understanding DHCP Servers -  Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
 Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
Dynamic Host Configuration Protocol or DHCP servers are the dedicated computers that have network operating systems installed on them and are responsible for providing automatic IP addresses to all the client computers that are configured to obtain the addresses automatically.
Understanding DNS Servers -  Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
 Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Domain Name System or DNS servers are dedicated computers that have network operating systems installed on them and are responsible for resolving hostnames (computer names) to their IP addresses and vice versa. DNS servers are used worldwide and are helpful while accessing the Internet and visiting websites. Every Internet Service Provider or ISP has its own DNS server which receives name resolution requests from the subscribers of that ISP and resolves the requested host names to their corresponding IP addresses.
Understanding DNS Updates & DNS Records -  DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
 DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
DNS records are the objects that are created either manually by the DNS administrators or automatically by the DNS servers themselves. A DNS server can have indefinite numbers of records and each DNS record is helpful in resolving the query of its own type. For example a Host (A) record in DNS server helps resolving a hostname to its corresponding IPv4 address whereas Host (AAAA) record resolves hostname to its corresponding IPv6 addresses.
Living La Vida Wireless -  Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
 Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
Do you often feel tethered to your home computer or other electronic devices? Tired of the endless cords to untangle under your office desk? Then it's time to go completely wireless! It's easier than ever to live a completely wireless lifestyle, thanks to innovations in the consumer and business electronics industries. Review some of the latest gadgets and services that will have you free-wheeling it in no time.
Understanding DNS Zones -  When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
 When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
When a DNS server role is installed on a network operating system, by default forward lookup zone is automatically created and the DNS server works as Caching Only server that caches the results of all the queries that it resolves. Forward lookup zone of a DNS server resolves IP addresses to their corresponding host names, is used in most network setups in production environments.
Understanding DHCP Classes -  In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
 In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
In small-scale organizations and home environments, DHCP servers are installed normally and no class oriented configurations are done. The reason behind this is that by default all DHCP client computers belong to default DHCP class and as soon as DHCP scopes are configured and the DHCP servers become ready to assign dynamic addresses to the client computers, the DHCP clients start receiving the IP addresses without any additional administrative overheads. However, in order to allow DHCP servers to assign different ...
What is Computer Networking?
A network is a collection of connected intelligent computing devices. The connection is not necessarily a fancy one. A connection between two computers by direct cabling is qualified to be a network. By this definition, a workstation which is loaded with a computer, a scanner, and a printer, is not treated as a network.A network can consist of two computers connected together on a desk or it can consist of many Local Area Networks (LANs) connected together to form a Wide Area Network (WAN) across a continent. The key is that two or more computers are connected together by a medium and are sharing resources. These resources can be files, printers, hard?drives, or CPU number-crunching power.
A Local Area Network (LAN) is a smaller network within one location or between several buildings A Metropolitan Network (MAN, politically incorrect, no WOMAN!) is a midsize network spanning the city. A Wide Area Network (WAN) is a giant network spanning across several cities or even several continents.
|



No comments:
Post a Comment